 |
hack wifi password |
We
are using Kali Linux in this tutorial for hacking wifi password but you
can choose any distribution as long as all the tools we are using here
are configured there. Wifi password hacking process is easy, But it
takes more time than any other wifi hacking Process because we have to
do a brute force in this method of wifi hacking but there are various
other methods to crack a wifi password using a Linux distribution and we
are going to discuss all of the methods in details with which a hacker
can hack a wifi password so sit tight and read it all till end. Most
of the people are very much interested in hacking the Wi-Fi networks,
but it may not be for illegal activities. Strong Encryption techniques
have been developed in order to secure Wi-Fi networks. There are
different types of Encryption from which three basic security encryption
are most common. Before
cracking a Wi- Fi network, you must be aware of basic encryption
techniques that protect a Wi-Fi network. These three methods of
encryption are the major sources of vulnerability associated with
wireless networks. The different types of Wireless Encryption Security techniques include the following:
Wifi Password encryptions
WEP:
WEP is Wired Equivalent Privacy that can be cracked easily when
configured appropriately. This method of encryption can be cracked
within few minutes.
WEP is Wired Equivalent Privacy that can be cracked easily when
configured appropriately. This method of encryption can be cracked
within few minutes.
WPA:
WPA is Wi-Fi Protected Access that provides strong security. Even then,
there is the possibility to crack if the Wi-Fi password if short.
However, wireless networks can be hacked easily using various tools.
WPA is Wi-Fi Protected Access that provides strong security. Even then,
there is the possibility to crack if the Wi-Fi password if short.
However, wireless networks can be hacked easily using various tools.
WPA2:
WPA2 is Wi-Fi Protected Access 2 that also eventually provides high
security. You can hack this method of Wi-Fi encryption at the time of
packet generation from Wi-Fi access points.
WPA2 is Wi-Fi Protected Access 2 that also eventually provides high
security. You can hack this method of Wi-Fi encryption at the time of
packet generation from Wi-Fi access points.
Required components to hack wifi password
Kali Linux OS
Kali Linux is a bootable Linux distribution with lots of pen-testing tools and is almost needed for all hacking article at ndm-news So, if you have not installed it. Then please download and installed it from the official site.Kali Linux Rolling 2016.2 version is released now.This OS will go through all the methods.You can use other OS to but i will recommand this OS because Kali Linux has every thing preconfigured
Wi-fi Network Card
If you are on laptop and have wifi card in it then that will work
because pretty much all wifi cards are compatible with Kali but if you
have a desktop then you will need an external Wifi adapter I will
recommend buying Alfa AWUS036NH this wifi card has every functionality you ever going to need during the wifi hacks.
Laptop or PC
Without laptop or pc you will not be able to hack wifi password or
atleast WPA protected password without any WPS enabled on it.
Your
can “guess the wifi password” because sometimes this saves you from a
lot of trouble that you will go through in a process of hacking wifi
passwords.The first method that we are discussing here is wifi WPA2
password cracking using the Aircrack-ng suite.
Hack Wifi Password using Aircrack-ng suite
The process is done by aircrack-ng suite if you don’t have already
installed then download it from the official repository and if you have
kali Linux installed then you don’t have any worries regarding hacking
tools.
Boot into Kali Linux
You can boot into kali Linux as a live boot or if you have installed
kali Linux on your system then you direct fire up the kali Linux
Gather Information
Before launching the attack you need to know about your wireless network
interface name, make your wireless card is in monitor mode. Then get
the BSSID ( it is the series of unique letters and number of a
particular router) of the access point. So let us do all these things.
Find your wireless card
Inside terminal or console, type:
airmon-ng
There you should see a list of interface names of different devices.
There should be a wireless device in that list you have connected it to
Kali Linux.You will get your wifi card as Wlan0 if you have not created a
monitor interface yet.
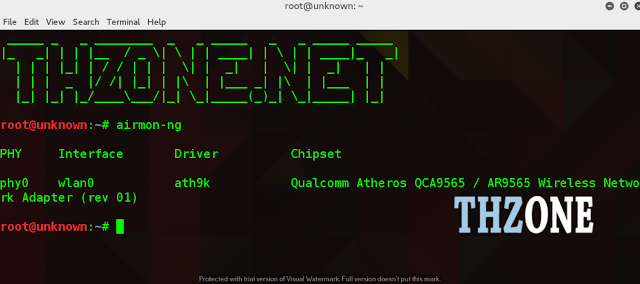
airmon-ng
Kill the process that can stop us from monitor mode this can be done by following command
airmon-ng check kill
Enable monitor mode
Supposing your wireless card interface name as wlan0, type this command in that same console.
1
airmon–ng start wlan0
This code will create a new monitor mode interface wlan0mon like in the screenshot below which you want to keep note of.
Now Type the following command to get a view on the air around and check who is connected to the wifi routers around you
airodump-ng wlan0mon
airmon-ng wlan0mon
Search the BSSID and channel of the Access Point
Now let’s find the information. Type the following Command in terminal
1
airodump–ng wlan0mon –c 6
If you are on laptop and have wifi card in it then that will work
because pretty much all wifi cards are compatible with Kali but if you
have a desktop then you will need an external Wifi adapter I will
recommend buying Alfa AWUS036NH this wifi card has every functionality you ever going to need during the wifi hacks.
Laptop or PC
Without laptop or pc you will not be able to hack wifi password or
atleast WPA protected password without any WPS enabled on it.
Your
can “guess the wifi password” because sometimes this saves you from a
lot of trouble that you will go through in a process of hacking wifi
passwords.The first method that we are discussing here is wifi WPA2
password cracking using the Aircrack-ng suite.
Without laptop or pc you will not be able to hack wifi password or
atleast WPA protected password without any WPS enabled on it.
Hack Wifi Password using Aircrack-ng suite
The process is done by aircrack-ng suite if you don’t have already
installed then download it from the official repository and if you have
kali Linux installed then you don’t have any worries regarding hacking
tools.
Boot into Kali Linux
You can boot into kali Linux as a live boot or if you have installed
kali Linux on your system then you direct fire up the kali Linux
Gather Information
Before launching the attack you need to know about your wireless network
interface name, make your wireless card is in monitor mode. Then get
the BSSID ( it is the series of unique letters and number of a
particular router) of the access point. So let us do all these things.
Find your wireless card
Inside terminal or console, type:
airmon-ng
There you should see a list of interface names of different devices.
There should be a wireless device in that list you have connected it to
Kali Linux.You will get your wifi card as Wlan0 if you have not created a
monitor interface yet.
 |
| airmon-ng |
Kill the process that can stop us from monitor mode this can be done by following command
airmon-ng check killEnable monitor mode
Supposing your wireless card interface name as wlan0, type this command in that same console.
1
|
airmon–ng start wlan0
|
This code will create a new monitor mode interface wlan0mon like in the screenshot below which you want to keep note of.
Now Type the following command to get a view on the air around and check who is connected to the wifi routers around you
airodump-ng wlan0mon |
| airmon-ng wlan0mon |
Search the BSSID and channel of the Access Point
Now let’s find the information. Type the following Command in terminal
1
|
airodump–ng wlan0mon –c 6
|
Search the BSSID and channel of the Access Point
Now let’s find the information. Type the following Command in terminal
1
|
airodump–ng wlan0mon –c 6
|
 |
| airodump–ng wlan0mon –c 6 |
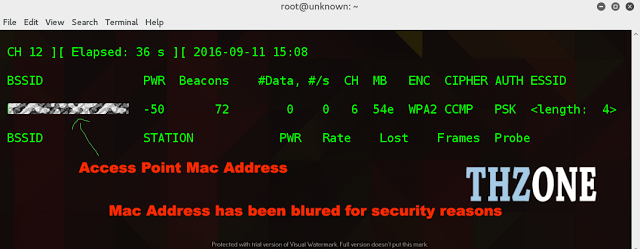
Then you will see a list of Wireless Networks available around you and
please keep note of the BSSID and channel of the ESSID (wireless
network) you want to crack. Please note that the less the number is in
the PWR column the close you are to the router; example mine is (-42)
which means I am quite near to the router. When you find it hit CTrl+C
to stop it scanning and enter the following:
1
|
airodump–ng —bssid (AP BSSID address) –c (chaneel no) –w (file name you want to save with) (monitorinterface
|
So, in my case, it will be
1
|
airodump–ng —bssid 54:E6:FC:E0:AC:FC –c 1 –w thzone wlan0mon
|
Hacking thzone.cap file with aircrack-ng
Now, its time to capture a handshake so that we can use it to get the
plain password of the network. Here is a little tricky part, if there is
a client connected to the network then there will a mac address listed
in the “station column” like in the screenshot below and if not then you
will have to wait for someone to connect it to get the 4-way
handshake.You will get the handshake if anyone tries to connect to that
network.
But, if there is someone connected to the network then you can
de-authenticate him so that he will try to reconnect and you will be
able to get the handshake. To de-authenticate him enter the following
code in a new console. But, before taking note of the Mac Address of the
station.
1
|
aireplay–ng –a (BSSID of the network) –c (MAC address of the client) –0 20 (for deauntheticate “20” forno of packets to send) (monitor interface)
|
You can send any no of packets but few packets would be enough. In the
image, I have sent 20 packets it is better you send few packets and only
and if you don’t get the handshake you can hit Ctrl+C to stop the
process and redo it again.
1
aireplay–ng –a 54:E6:FC:E0:AC:FC –c 9C:4E:36:4E:F5:F0 –0 20 wlan0mon
|
Now it will send deauthentication packet and if you are close to the
network and if everything goes right then he will get disconnected and
will try to connect again and we will get the 4-way handshake file in
the top right corner of the airodump screen as shown below. But, the
client should also be physically close to your wireless adapter network
range so that it can de-authenticate them.
Cracking the password from .cap file
Now it’s time to crack the 4-way handshake which is little difficult to
do. There are lots of ways to do it but I will show you the simple one.
First, let us see where is our saved .cap(4-way handshake) file so please enter the following:
1
|
ls
|
It will show you the list of files in your Desktop in the terminal. The
screen would look like this.or you can check directly by browser like in
screenshot
Now, lets brute force the thzone.01.cap file using aircrack-ng. You will
need a Dictionary or word list file to get it work. There are few of
them already in the Kali Linux but you can download more. Aircrack
simply tries to match the word from the dictionary to the .cap file and
if matched then it will show the password but if the word is not in the
dictionary then it will fail. We are using the thzone_wordlist.txt
password list which can be found in ‘/root/thzone_wordlist.txt” of Kali
Linux you can create your own wordlist by using the following tutorial
on wordlist creation in kali Linux. Enter the following command
1
|
aircrack–ng –w (location of the password list) (cap file *.cap)
|
In my case,
1
|
aircrack–ng –w ‘/root/thzone_wordlist.txt’ thzone.01.cap
|
Depending upon the speed of your CPU and the size of the password file
it could take a lot of time. The -01 is automatically added by the Kali
Linux and everything is case sensitive. After executing this command the
screen will look like this.
If the key is found then it will say, “KEY FOUND!” and if not it will
say, The pass-phrase is not in the Dictionary or something like this.
So, if it is not found then you can try to bruteforce it by trying every
combination of word (as we create in kali Linux wordlist tutorial)
which will take lots of time.
Hack Wifi Password using Reaver
Let’s hack wifi password using reaver
- Reaver (support for all routers)
As reaver is already installed in kali Linux We should get to the
process of wifi password hacking.If you have root access to kali Linux
then you can use commands without sudo and if you are a simple user then
you should use these commands
sudo iwlist scan wlan
Set your device into monitor mode.
sudo airmon-ng start wlan0
Run the tool against an access point.
reaver -i wlan0mon -b <MA:CA:DD:RE:SS:XX> -vv
Wait until it finishes.Now the hacking with reaver ends here it surely
takes hell of lot time to hack a WPS pin lets try with wpcrack.py
Hack Wifi Password using wpcrack.py
Wpcrack.py is a program that makes the process of wifi password hacking easy let’s follow the tutorial
- wpscrack (faster, but only support for major router brands)
Let’s hack wifi password using wpcrack.py
sudo iwlist scan wlan0ip link show wlan0 | awk '/ether/ {print $2}'sudo airmon-ng start wlan0
1
|
wpcrack.py –iface wlan0mon –client <your MAC, because you‘re attacking yourself, right?> –bssid<AP MAC address> —ssid <name of your AP> –v
|
Hack wifi password using Wifite
Wifite is a Linux-based platform tool that is already installed on
variant Operating Systems like Kali, Backtrack 5, BlackBuntu, BackBox,
and Pentoo. Wifite is basically used to attack multiple encrypted
networks (WEP, WPA/WPA2, and WPS) in a row that is customized to be
automated with only a few arguments. Wifite is a wireless auditing tool
that aims to be the “set it and forget it” method of hacking.
Let’s hack wifi password using wifite
How to View Available Access Points?
- As you are using Linux Operating System, Initially go to Application.
- Now go to Kali Linux > Wireless Attacks > 802.11 wireless tools > Wifite.
- If you are unable to view Wifite then simply type ‘wifite’ in Terminal.
- Here, you can see List of Available Wi-Fi Access Points. (you must be root).
- Wait for few seconds in order to notice nearby Wi-Fi points like WEP, WPA/WPA2.
Hack wifi password based on WPS encryption using wifite
Hacking a Wi-Fi network that uses WEP security encryption is relatively
very easy when compared to other encryption methods. While using this
Wifite tool, you must follow simple steps as given below:
- Just choose the appropriate target NUM (1,2,3,..,n) in order to crack it.
- Hacking a WEP key that ensures 100% possibilities of cracking the WEP WiFi password that currently uses 5 attacks.
- Make sure that the attack is completed within 10 minutes.
- You need not worry if one WEP WiFi attack fails, the other will come into action automatically for succeeding 10 minutes.
- You can choose any attack. For instance, choose NUM 2 attack.
- Within few minutes the WEP Wi-Fi network gets hacked.
- That WEP Key can be used as the Wi-Fi password.
- Later, you can also convert the Wi-Fi password into the actual password that is in the form of human readable mode using online Hex-to-ASCII converter.
Hack wifi password using wifi-phisher
Wifi-phisher is a security tool that mounts the fast automated phishing
attacks which are against WPA networks so as the order to acquire all
the secret passphrase of the particular Wi-Fi network. Unlike other
methods of hacking, Wifi-phisher is a type of social engineering attack
that does not include brute forcing. It is very easy way to obtain WPA
credentials of the users whom you wish to hack. Wifiphisher also works
on a platform that supports Kali Linux Operating System and is licensed
under the MIT license.
Let’s hack wifi password using wifi phisher
Wifiphisher is a tool that is used to hack a Wifi network and this attack makes use of three phases:
Step 1 to hack wifi password using wifi phisher
- The victim is being de-authenticated from their access point.
- Wifiphisher tries to jam all the target access point’s wifi devices continuously that are available within range by sending deauth packets to the client from the access point.
- It discovers all the networks that are available in the access point range.
- This tool alters the access point of all the devices through the main server and broadcasts the address along with the deauth packets.
- It starts generating fake access points by copying an access point from a set of access points
Step 2 to hack wifi password using wifi phisher
- This is the second phase where the Victim joins a rogue access point.
- It asks for password authentication and in the backdrop, the tool tries to copy all the credentials of the possible Wi-Fi networks.
- Wifiphisher sniffs the area and copies the target access point’s settings.
- Now, this tool creates a rogue wireless access point that is modeled on the target by setting a NAT/DHCP server and forwards the right ports.
- Consequently, because of the jamming, clients will start connecting to the rogue access point. After this phase, the victim is under MITM.
Step 3 to hack wifi password using wifi phisher
- The victim is being served a realistic router config-looking page where the Wifiphisher tool employs a minimal web server that responds to HTTP & HTTPS requests.
- As soon as the victim requests a page from the Internet, wifiphisher responds with a realistic fake page that asks for WPA password confirmation due to a router firmware upgrade.
Hack Wifi Password Using coWPAtty
cowpatty (often
stylized as coWPAtty). This app simplifies and speeds up the
dictionary/hybrid attack against WPA2 passwords, so let’s get to it!
Open CoWPAtty in Terminal
cowpatty
Kali Linux will provide you a brief help screen. coWPAtty requirements to hack wifi password are following
start Monitor mode
airmon-ng start wlan0Set a Capture File
Next, we need to start a capture file where the hashed password will be stored when we capture the 4-way handshake.
airodump-ng --bssid 00:25:9C:97:4F:48 -c 6 -w cowpatty wlan0mon
This will start a dump on the selected AP (MA:CA:DD:RE:SS:XX), on the selected channel (-c 6) and save the hash in a file named thzone.
Capture the Handshake
Run the Cowpatty
Now that we have the hash of the password, we can use it with cowpatty and our wordlist to crack the hash.
cowpatty -f /root/thzone-wordlist.txt -r /root/thzone-01.cap -s Mandela2
As you can see in the screenshot above, now coWPAtty is generating a
hash of every word on our wordlist with the SSID as a seed and comparing
it to the captured hash. When the hashes match, it displays the
password of the AP.
Hack wifi password using fern wifi cracker
Fern Wi-fi Cracker can crack WEP,
WPA, and WPA2 secured wireless networks. Fern basically takes the
command line utilities to crack these networks and puts them in a GUI.
Very simple to use… scary easy! Fern also provides some extra
functionality for hijacking sessions and locating a computers
geolocation via its Mac address.
Plug in the USB wireless adapter (I’m using the Alfa AWUS036H 802.11b/g
USB wireless adapter) and open the Terminal and run iwconfig to verify
the USB adapter interface.
Select the Interface and Fern enables monitor mode. If your wireless
interface does not show in the list hit the Refresh button and try
again.
Before starting the scan double-click on any blank area of the Fern home
screen to bring up the Access Point Scan Preferences screen. You can
set the channel option to scan a single channel or leave it at the
default All Channels. One nice feature is to check the Enable XTerms
option which will have Fern open up the Terminal windows during its
usage to see what the program is doing in the background.
Back on the Fern home screen click the Scan for Access points button.
And another showing the WPA enabled networks. The top part of the WPA
Scan Terminal window shows the networks being found, and the lower part
shows any connected client devices. For a WPA attack to work, it
requires a connected client. The most important part of the attack will
kick the client off the wireless network and capture the 4-way handshake
when the client device re-authenticates to the network.
On Ferns home screen the networks being detected will start populating next to the WiFi WEP or WiFi WPA buttons.
Clicking on the WiFi WEP or WiFi WPA button will bring up the Attack
screen and the top pane will list the networks found. Select the AP to
crack, but before clicking the Attack button to the right let’s go over a
couple of settings.
I will use the Regular Attack option, but there is a WPS Attack option
and I believe Fern uses the Reaver utility to launch the WPS attack as
we have done above with reaver this tool will do it in gui and automate
the process.
Common.txt is the wordlist that comes with the Fern program, but any
wordlist you download or have created on your own can be used by hitting
the Browse button and pointing Fern to the alternative wordlist file.
With the Regular Attack and the wordlist selected hit the Attack button.
Fern will start the attack and on the left side of the screen, the
attack steps will turn yellow as Fern works through the various steps.
The most important step is capturing the 4-way handshake and Fern will
open an aireplay-ng Terminal window showing the progress of
deauthentication of the connected client.
It may take several attempts to deauth a client and capture the 4-way handshake.
Once Fern has captured the handshake it will start the brute force
attack. Viola! If the WPA key is in the wordlist being used it will
display the found key in Red.
As I mentioned I setup a passphrase I knew would be found quickly, and
from the start, to finish this attack took under 4 minutes!
Back on the Fern main screen is a Key Database button and it now shows one entry.
Clicking the Key Database button will display the found keys.
How to Protect your Wifi Network from getting Hacked?
From the above techniques, you might clearly understand that hacking a
Wi-Fi network is an easy process. Now, it’s time to focus on tightening
your Wi-Fi security. Now, you might get complete awareness about the
security and Wi-Fi Network Hacking through this article. Follow some
tips so as to enhance the security of your Wi-Fi network.
- As WEP is an easy hacked Wi-Fi security encryption method, it is recommended to change Wi-Fi security from WEP to WPA/WPA2. WEP has now denigrated security protection.
- Change the password of your Wi-Fi network periodically so that if in case someone gets the chance to hack your Wi-Fi password, they will not be able to use your free Internet for the long period of time.
- Disable WPS as it has lots of vulnerabilities.
- Using a common dictionary word for a WPA or WPA2 passphrase makes it easier to hack.
Tags
”hack wifi password, hack wifi password 2013, hack wifi password
2014, hack wifi password 2015, hack wifi password 2016, hack wifi
password aircrack-ng, hack wifi password coWPAtty, hack wifi password
fern wifi cracker, hack wifi password kali linux, hack wifi password
reaver, hack wifi password wifite, hack wifi password
wpcrack.py, hacking wifi password, how to hack wifi password”
Dapatkan Tips Menarik Setiap Harinya!
- Dapatkan tips dan trik yang belum pernah kamu tau sebelumnya
- Jadilah orang pertama yang mengetahui hal-hal baru di dunia teknologi
- Dapatkan Ebook Gratis: Cara Dapat 200 Juta / bulan dari AdSense











0 Response to "How to hack wifi password step by step tutorial (7 exclusive hacking methods)"
Post a Comment
Catatan Untuk Para Jejaker